AiTM phishing bypasses multi-factor authentication
Microsoft has recently published details of a massive phishing attack that targeted more than 10,000 organizations. The worrying details about this particular attack is how it manages to bypass 2-factor authentication by using adversary-in-the-middle (AiTM) phishing sites to steal passwords and session data.
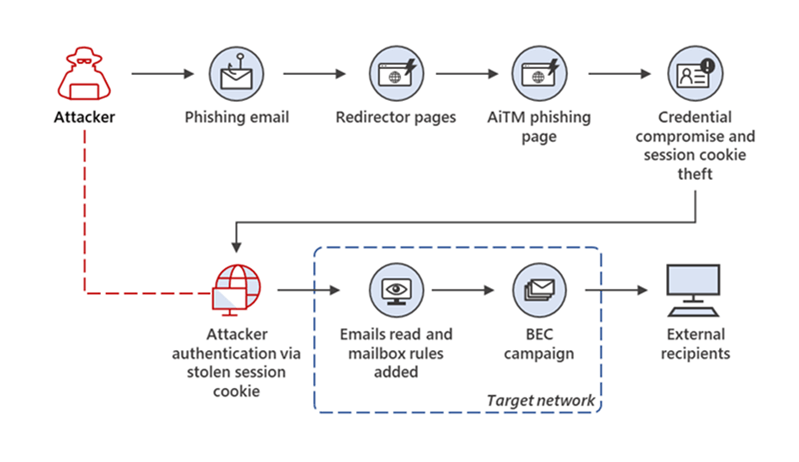
The malicious actors used adversary-in-the-middle (AiTM) phishing sites to steal passwords and session data; this allowed them to bypass multi-factor authentication protections to access user email inboxes and run follow-up attacks using business email compromise campaigns against other targets.
Adversary-in-the-middle Phishing
Adversary-in-The-Middle phishing attacks typically use proxy servers in-between the user and the website the attack is trying to compromise. If successfully routed through the proxy, the attacker can gain access to a password while the user thinks it is interacting with a Microsoft legit website.
AiTM phishing campaigns are one more example of how threats continue to evolve in response to the security measures and policies organizations put in place to defend themselves against potential attacks. Microsoft recommends to work with sites that support Fast ID Online (FIDO) v2.0 and certificate-based authentication. More information can be found here.
